CAcert.org
CAcert is a community-driven SSL certificate authority who issues free public key certificates signed by their root certificate. They have been trying to get their root certificate audited and included in major browsers for decades and it's not happening. Using their certificates is therefore pointless and certificates signed by CAcert should not be deployed on any public-facing services. You might as well use a self-signed certificate as modern browsers will produce the exact same "not valid" message whether you use a CAcert-signed certificate or a self-signed one.
Brief technical background[edit]
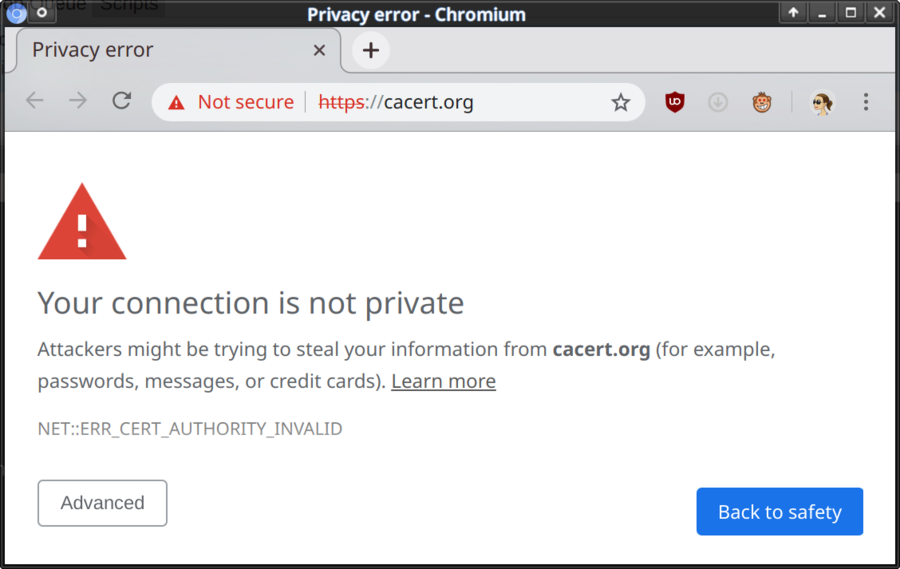
https works by web servers presenting a certificate to web browsers when they visit a website. The browser checks the certificates issuer or "signer", if anyone actually signed it, against a list of approved "authorities". The site's presented with a lock in the URL address bar if the certificate is signed by an "authority" in the list and the certificate is valid for the domain visited during the visit's time-frame. The following misleading message is presented if it's not signed by someone approved OR there is another problem such as the certificate being valid until 2012 and it's way past 2012:
CACert has managed to get their certificate included in a few Linux distributions like Gentoo, Arch Linux and Knoppix. However, as their InclusionStatus page shows: Major browser vendors do not include their certificate. This means that the vast majority of people visiting a site using a SSL certificate signed by CACert will get the above misleading message and turn away. We say misleading because the statement "Your connection is not private" is simply not true; the "ERR_CERT_AUTHORITY_INVALID" - certificate authority did not pay us millions to pretend there's security - is the real reason why the message is presented.
Browser Approval: It's NOT happening[edit]
CACert has been trying to get their service approved and their root certificate included in major browsers for almost two decades. It's just not happening.
CAcerts request to have their root certificate included in Mozilla Firefox was opened all the way back in August 2003. That request was put in "restricted comments" mode in 2013. There has not been any activity since.
There does not seem to be any progress in getting the CAcert root certificate into Google Chromium (the free software browser Chrome is based on).
Free alternatives[edit]
Let's Encrypt, sponsored by major corporations like Mozilla, Google, Cisco, IBM/RedHat and others hand out free certificates left and right with little hassle. The major downside to using their service is that certificates are only valid for 90 days. While this may seem problematic it's not really, it only takes a monthly cron job to renew issued certificates. You can learn more about their service at letsencrypt.org.
HOWTO use CAcert[edit]
You can install CAcert's root certificate in your own web browser and use their SSL certificates on your own sites without getting any warning. As stated above: Using it on some public service with random visitors is a bad idea - unless you only cater to Arch Linux users.
Getting a CAcert certificate is fairly easy, just go to their website cacert.org, sign up, verify some e-mail account and send them your certificate request and get a cacert signed certificate by e-mail. You can also copy and paste it off their site.
Do keep in mind that there really isn't that much difference between a self-signed certificate and one issued by CAcert. Only users who have manually installed the CaCert root certificate in their browser or use Arch or Gentoo will have CAcert certificates accepted. Everyone else will get the "Not private" warning.
A certificate request can be generated by running this command:
openssl req -nodes -new -keyout private.key -out server.csr
openssl will ask all kinds of questions when you run this command. Just ignore everything until you get to "Common Name". Enter the domain name you will use the certificate for as your answer to "Common Name". It would be something like www.yoursite.tld or *.yoursite.tld. OpenSSL will create a file called server.csr (or whatever you put after -out). This is your "request" which you need to cut and paste into a form on CAcert's website. They will sign this request and give you a certificate you can cut and paste into a configuration file.
Sad post-script[edit]
This particular page was originally created in January 2007. It is quite sad that it's 2020 and CAcert's made zero progress in getting their root certificate approved for inclusion in major browsers.
The situation for free SSL and https for everyone has, of course, improved with the advent of letsencrypt.org which is run by "A better Internet". It's still sad that CAcert's essentially dead. It would be nice to have an alternative to LetsEncrypt, "A better Internet" could easily start deciding that the Internet would, in their opinion, be better without website which exposes illegal or immoral actions by one or more of their sponsors (the amount of criminal enterprises sponsoring that group is quite concerning).

Enable comment auto-refresher